Secure BYOD Enablement for the Modern Workforce
Venn’s Blue Border™ securely enables BYOD workforces on any PC or Mac. No costly infrastructure. No frustrating remote apps. No need to buy, lock down and ship computers.
Welcome to the future of work.
Blue Border™
Venn’s Blue Border is the first purpose-built software for securely enabling BYOD workforces. Similar to an MDM solution but for laptops – work lives in a company-controlled Secure Enclave installed on the user’s PC or Mac, where all data is encrypted and access is managed. Work applications run locally within the enclave – visually indicated by a blue border – isolating and protecting business activity from any personal use on the same computer. Company data is secured without controlling the entire device while ensuring end-user privacy for everything outside the Blue Border.
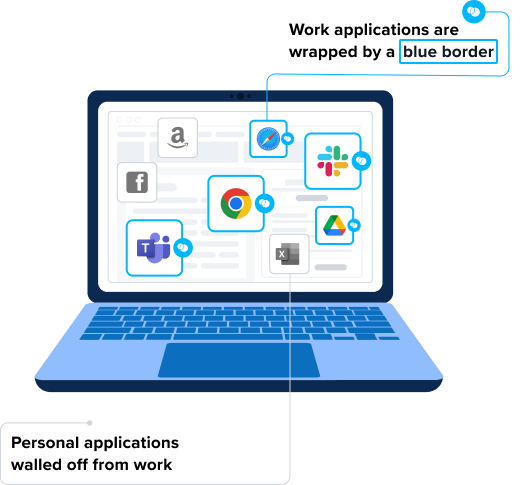
What Happens in Blue Border, Stays in Blue Border
With Venn, anything a user does inside Blue Border is protected and secure from anything a user does on the personal side. Anything a user does personally on their laptop outside of Blue Border is not going to be seen, tracked, or monitored by Venn.
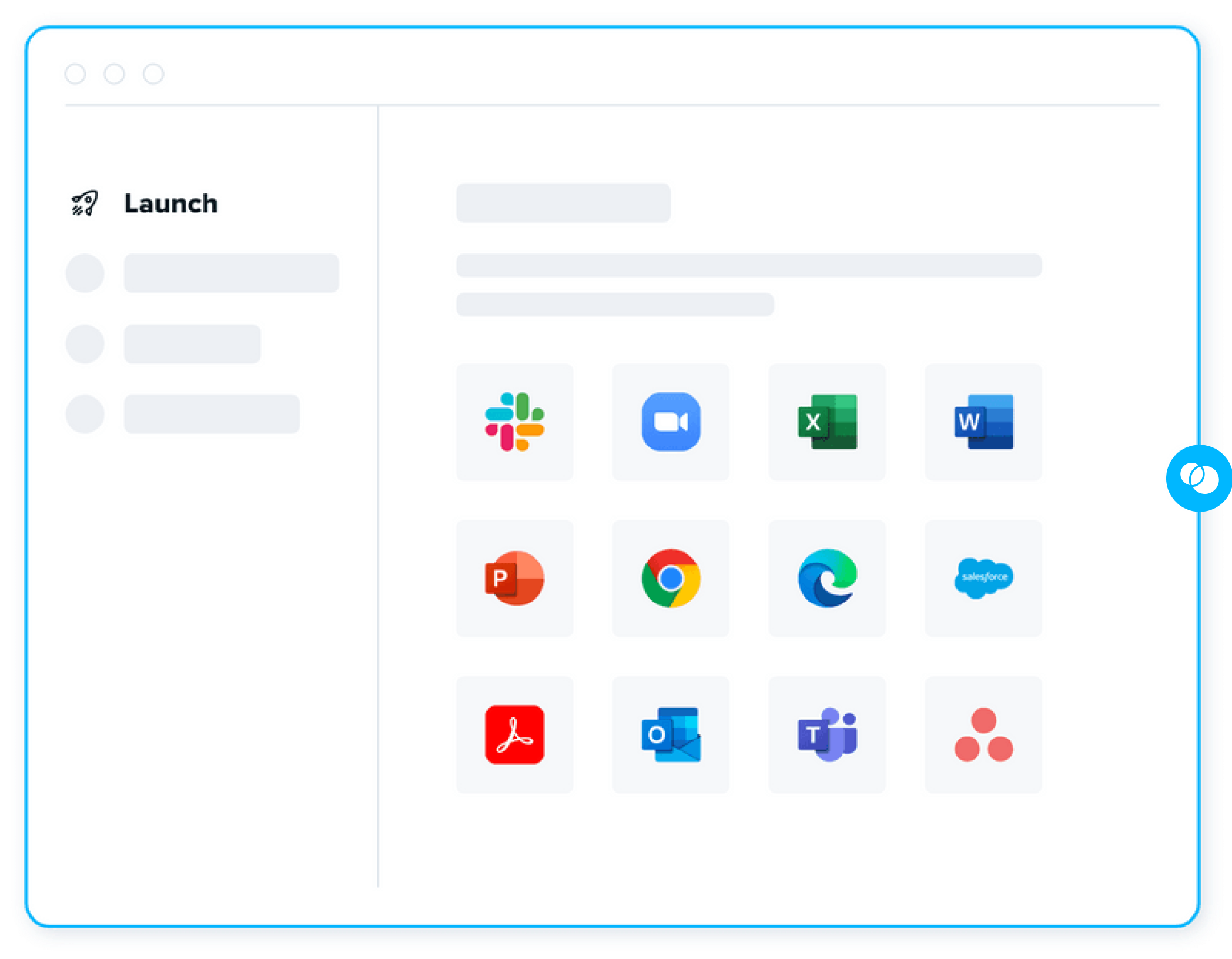
Local Applications Unencumbered
Protect any locally installed app for work including Chrome, Adobe, Slack, Microsoft 365, web conferencing software (Zoom, Teams, etc.) and more.
Apps run inside Blue Border so you don’t have to choose between local performance and safeguarding sensitive data.
Simplified Administration
With Venn, companies can onboard and offboard remote workers in minutes. Centralized administration simplifies management, offering complete visibility and control over your BYOD workforce. Gain real-time insights into user activity and device compliance, so you always know where, when and from what device a user accessed an application or sensitive data. Plus, with comprehensive compliance–ready logging, staying audit-ready is easier than ever..
Optimal Performance and Experience on any PC or Mac
Unlike VDI, which often suffers from latency and performance issues, Venn allows work applications to launch directly from the user’s computer, running locally instead of through a remote desktop. This ensures optimal performance and a seamless, familiar experience for users.
VDI Alternative
IT teams can easily support BYOD workforces without the cost, complexity, and usability challenges of VDI.
Corporate Device Freedom
Get out of the hardware business. Reduce or eliminate the cost and complexity of buying, managing and shipping company-owned PCs and Macs.
Zero Backend Infrastructure
Venn is revolutionizing how businesses enable BYOD workforces, removing the burden of buying and securing laptops or dealing with virtual desktops.
Venn is not a virtual desktop and requires zero backend infrastructure.
Purpose built with the
highest standards
Venn was built to comply with the strictest
cybersecurity standards including:
- SOC 2 Type II
- HIPAA
- SEC
- FINRA
- NAIC
- NYS DFS
- Mass 201 CMR 17.00
- CMMC
- PCI

How It Works
When a user launches a work application, Venn puts a virtual wrapper around it, visually indicated by a blue border around each application window. That work application is then running inside of the Secure Enclave, which acts like a firewall, controlling what can go in or out.
1

Launch Blue Border™ from any device
2

Blue Border™ kicks in and automatically detects work apps
3
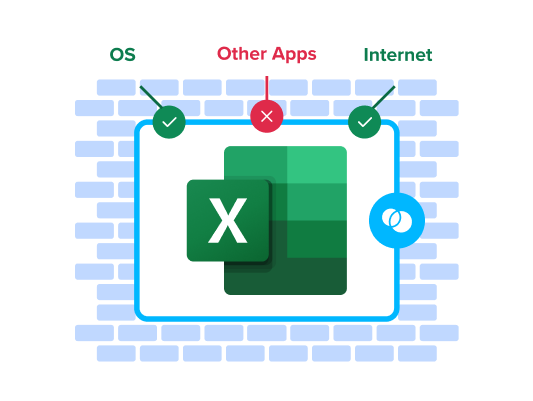
Blue Border™ acts a firewall to safeguard work apps and data
4

Work comfortably from any device with guaranteed compliance and regulations
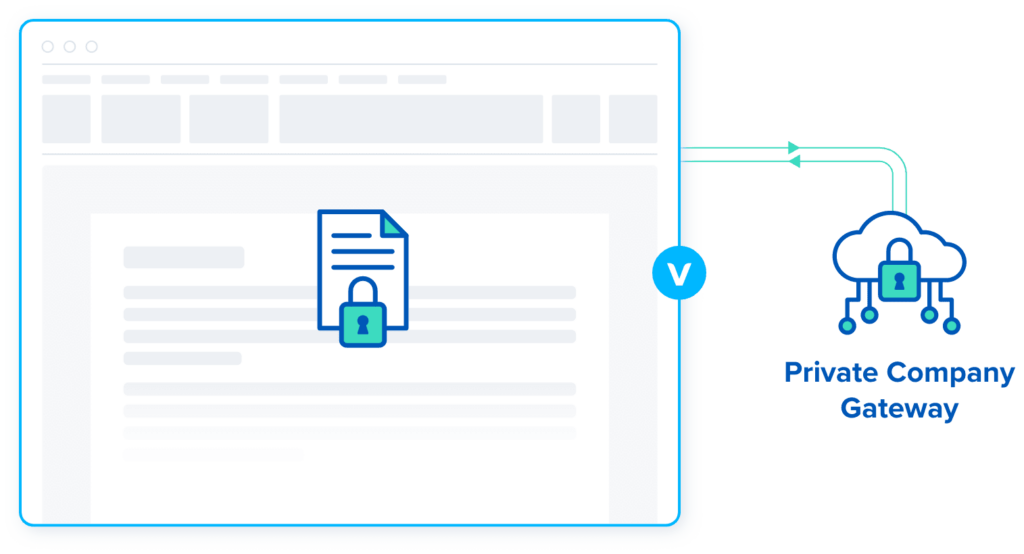
Data & Traffic Isolation
Data stored in Venn is always encrypted and inaccessible to any application outside of the enclave, while data in transit is routed through a built–in encrypted private company gateway or a VPN/network security system already employed by your organization. Access to Venn can be enabled, suspended, terminated or data remotely wiped, with a click of a button.
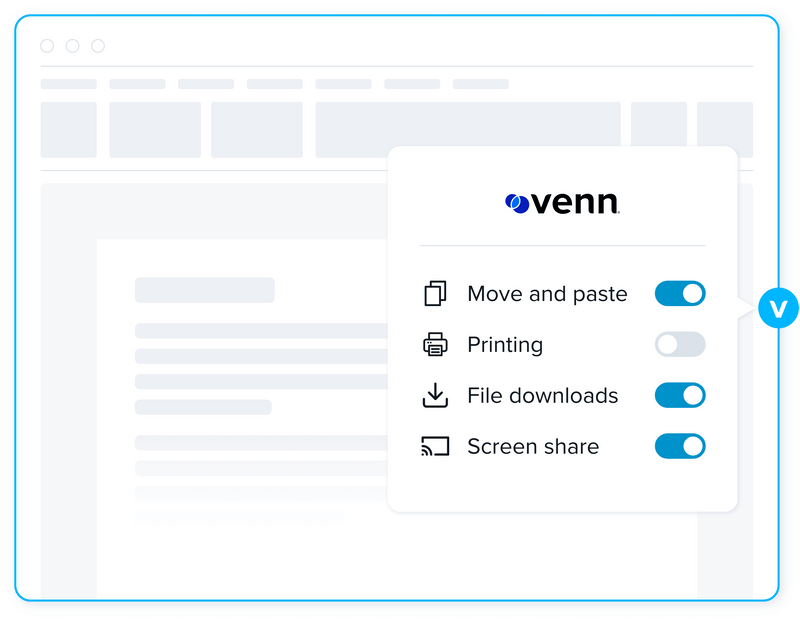
Fine-Tune Policy
Configurable policies allow you to control which applications are purposed for work, and only applications assigned to a user by an admin are permitted to run inside Venn. Applications have admin configurable DLP policies that govern functions such as copy/paste, screen sharing, printing, downloads and more.
Embrace and Optimize Your BYOD Workforce
Venn’s mission goes beyond merely securing BYOD; we aim to empower our customers to fully embrace and optimize BYOD. To achieve this, we’re continuously enhancing Blue Border with advanced tools and controls that tackle the common challenges of BYOD.
Managing a BYOD Workforce is about more than security
Tools for reducing friction and simplifying BYOD adoption.
Software Distribution
Venn Application Delivery ensures that applications are swiftly deployed and consistently maintained across all Venn-enabled devices.
Daily Device Checks
With Venn ReadyBlue, device status snapshots allow users and IT teams to quickly identify and resolve issues, keeping operations smooth.
User
Privacy
Venn Privacy Shield embodies our commitment to privacy through innovative architecture and patented technologies, protecting user privacy outside Blue Border.
Onboarding Assistance

Venn Onboarding process includes technical assistance available to all new users.
Before Venn, we were not allowing BYOD or unmanaged laptops and we were deploying computers for every person. Our struggle was because of all of our security tooling. To meet our benchmarks, we had to buy 1,000 dollar laptops to meet all the requirements and make it so that they could work. If we can get rid of just a portion of our laptops a year, it basically pays for all Venn users.

